IdentityForce: Mobile App
I joined two brilliant UX Designers in a three-week project to consider how IdentityForce could motivate its current customers to take small actions, on a regular basis, that would help them be more proactive in managing and protecting their identity.
We started by researching the industry, learning about IdentityForce’s products, best practices in identity management, and different factors that could trigger and motivate users to take actions. Through online surveys and face-to-face interviews with former victims of identity theft and industry experts, we were able to focus on the most common pain-points of our potential end users.
We then gathered our research findings and created a new and improved native mobile App, that through gamification, it would educate, influence, and motivate our users to be proactive in protecting their identity. We shared our solution with potential end users and made improvements based on the feedback we received.
Steven Bearak, the CEO of IdentityForce, was very impressed by our work, as we had solved one of the biggest challenges the company is currently facing, which is educating and motivating millennials when it comes to managing their own identity.
IdentityForce Mobile App
Selected Screens
Research:
Who is IdentityForce?
We started by exploring IdentityForce’s website, mobile App, and mobile web. We found out that while Identity Force is considered as the leader in identity and credit protection and is doing a great job in helping victims with recovery from identity theft, it does not take a lot of actions to prevent identity theft. However, Identity Force offers a lot of tools, resources, and useful tips that if they were presented to its users in a fun and digestible way, it could educate them and help them create new habits in monitoring and protecting their identity.
Challenge
How might we improve IdentityForce's product to increase users engagement in protecting their identity?
Hypotheses
Through gamification, we can create motivation and provide knowledge to empower our users in self-efficacy in protecting themselves as well as their loved ones.
And the Competitors?
Lifelock
Based on our research, Lifelock is IdentityForce’s main competitor. Lifelock helps its clients with Theft prevention by offering various tools, alerts, and the option to connect with live agents that can explain the significance of alerts to its clients. Lifelock was sued by the FTC in 2015 for failing to secure customers’ personal data up to advertised standards. Since then, LifeLock has been acquired by cyber security giant, Symantec. In contrast with Identity Force, Lifelock does not offer recovery services to its customers.
ID WatchDog
ID WatchDog beats all its competitors by offering rehabilitation for pre-existing theft, before the customers join its Web Application. The users could find suspicious items on their credit reports, or discover a warrant out for their arrest, before enrolling in ID Watchdog, and it will still work on their behalf to remove it by using power of attorney. They don’t seem to have a native mobile App.
Credit Sesame
Credit Sesame offers free identity theft protection with $50,000 insurance without taking credit card information and also a premium “full-service white glove identity restoration” and stolen/lost wallet protection, in which the company cancels and replaces all victim’s credit cards and IDs for them. The company claims it would take over locating the phone numbers, waiting on hold with banks and agencies, and requesting replacements, patching the victim in only for the times when needed.
ID Card
Identity Guard monitors the basics of users’ identity; name, Social Security number, bank accounts, credit reports, etc. Identity Guard offers powerful credit monitoring at extra cost. Its restoration services are not strong. Beyond identity theft insurance and a support hotline, most of the burden of restoring users’ identity is on them.
Behavioral Analysis
After our initial research, we started asking ourselves how we can motivate our users… How is it that some people are on top of managing their identity, and some are not even motivated to take the smallest steps when it comes to protecting their identity?
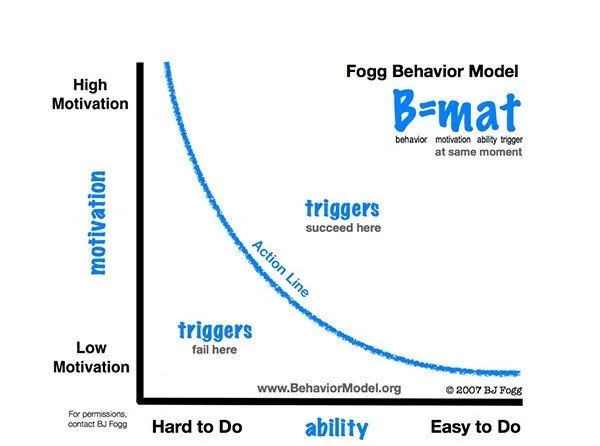
BJ Fogg’s Behavior Model suggested that three factors have to happen at the same time in order for people to change a behavior:
1) They need to be motivated
2) They need to have the ability to do the task they need to do
3) They need to be triggered to perform the behavior
Different people value different factors that make them do the things they do. Our study suggested that if we connect the new behaviors that we want our users to adapt to their values, more people would be motivated to try those behaviors that could eventually turn into long-lasting habits.
IdentityForce Mobile App
Behavioral Analysis - BJ Fogg's Behavior Model
Online Survey
To find out how people feel about identity protection and what actions they were(not) taking to manage their identity, we created an online survey and interviewed two victims of identity theft and two experts in the field, which helped us identifying our users, their challenges and their pain, and how we could help them.
Our survey had two series of questions:
1) General Behavioral Questions: The purpose of creating these questions was to find out the factors that could motivate or trigger people into wanting to change a certain behavior. We asked the participants to remember the most recent time they decided to achieve a goal, how they felt about achieving their goal, if they had to change their routine or create a new plan in order to reach that goal, if they monitored their progress, if they had to overcome any challenges in order to achieve those goals, if they were or were not successful in achieving their goal, and how it made them feel.
30 people participated in our study:
96.7% stated that in order to achieve a new goal in the past, they had to change their routine
76.7% said that they made a new plan to be able to make those changes
73.3% tracked their progress, using multiple tools
IdentityForce Mobile App
Behavioral Survey Questions
Affinity Map
We used Affinity Mapping technique to identify patterns that had made our survey participants decide to set a new goal in order to change their routine. We found out that the desire to change either comes from external factors or internal ones, and it either has a focused or exploration origin at the core.
IdentityForce Mobile App
Affinity Map
2) Specific Identity Management Questions: The purpose of asking these questions was to find out how our participants felt and how informed they were about identity management. We asked them how secure they thoughts their online presence was, if they were taking any actions to protect their identity, if there were any factors that were motivating them to protect their identity, if they were using any services to manage their identity, if they were a victim of identity theft or knew someone who had experienced it, and we asked them to name a few services that are offered to protect the users’ identity.
30 people participated in our study:
100% of the participants had heard of identity theft
When we asked how secure they felt about their personal online information:
Only 6.7% felt Very Secure
33.3% felt Somewhat Not Secure
26.7% felt Somewhat Secure
26.7% felt Secure
6.7% felt Not Secure
When we asked how often our participants changed their passwords:
Only 6.7% responded Every 3 Months, which is the recommended length
63.3% responded only when they are forced to
And 6.7% responded Never
IdentityForce Mobile App
Identity Specific Survey Questions
Out of 30 participants, 50% were actively taking actions to protect their identity
26.3% were considering using an identity protection service (73.7% weren’t)
73.3% had been or knew someone who had been a victim of identity theft (26.7% didn’t)
46.7% knew about identity protection services (53.3% didn’t)
IdentityForce Mobile App
Identity Specific Survey Questions
Interviews
Victims, Noop and Expert, Not Motivated
We interviewed two victims of identity theft. They both recalled how the experience made them feel vulnerable and unprotected, how frustrating it was to go through the experience, and how shocked they felt when they realized how easy it was for the hackers to get a hold of their information. To our surprise, they were not taking any actions to prevent that experience from happening again. They both mentioned that the financial damages were covered by their banks and that “lightning does not strike twice”.
Non-victims, Experts, Highly Motivated
We interviewed a former tax expert. She recalled how she felt every time she had to educate and help victims of identity theft, how she wished there were programs that would educate people to help reduce their chances of becoming victims, how frustrating it was to see victims going through the experience, and how she wished she knew more in order to protect herself and her loved ones from becoming victims. To our surprise, besides changing her passwords every once in a while, she was not taking any significant actions to protect her identity either.
For our last interview, we spoke to a software engineer, who was well-informed about identity protection. He was very proactive in terms of managing his identity online and offline. He knew a lot about best practices and even gave us tips to protect our own identity. He also suggested a few features that we could consider to include in our solution to help users manage their identity. He, however, did not like our gamification concept, as he was already motivated and was only interested in accessing the information that Identity Force would provide.
Empathy Map
This beautiful bouquet of post-it sums up our interviewees’ response to our questions and shows their thought process. Gathering the result of our interviews, survey, and our secondary research helped us create four personas that our App could be targeting.
IdentityForce Mobile App
Empathy Map
Personas
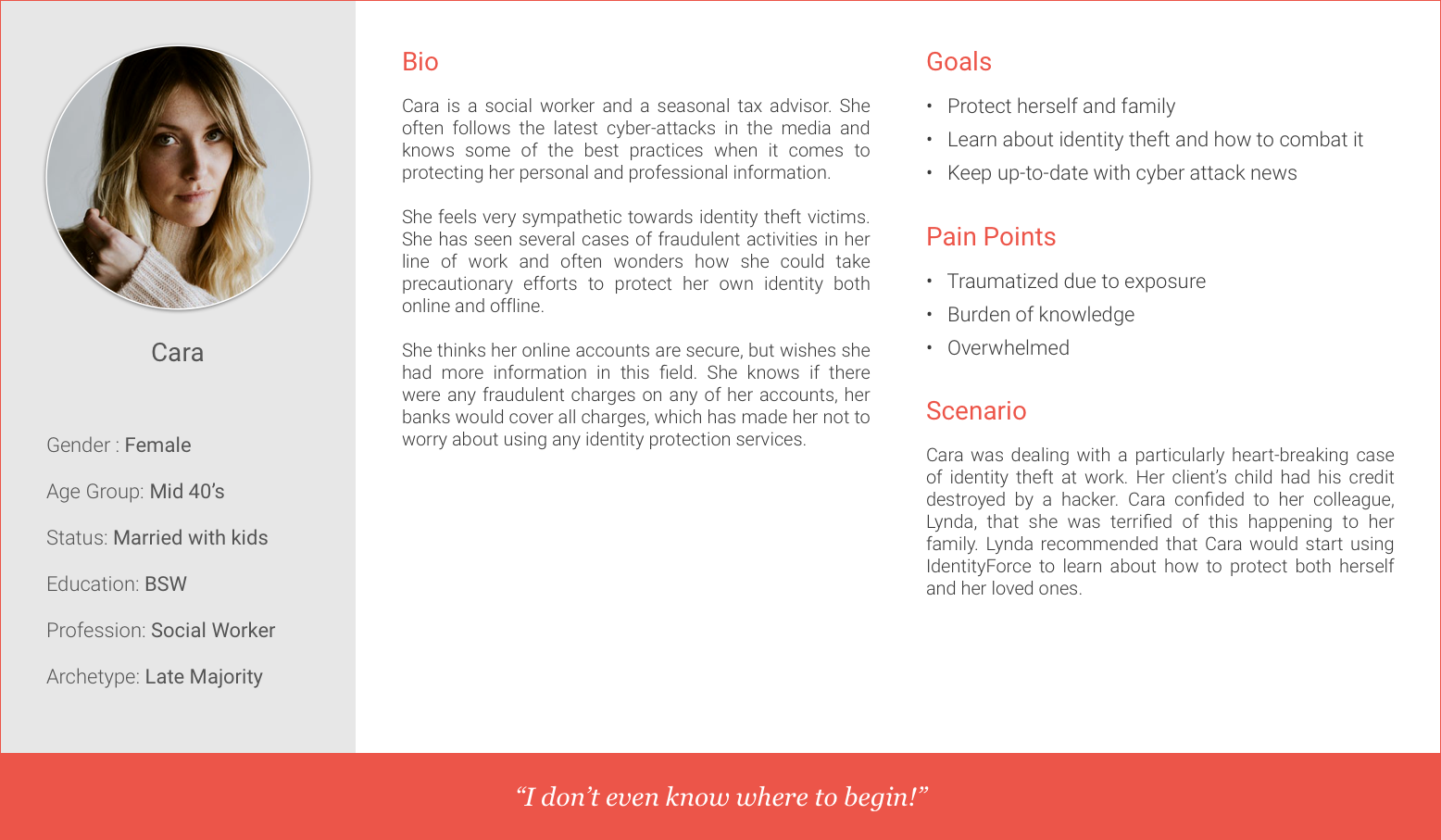
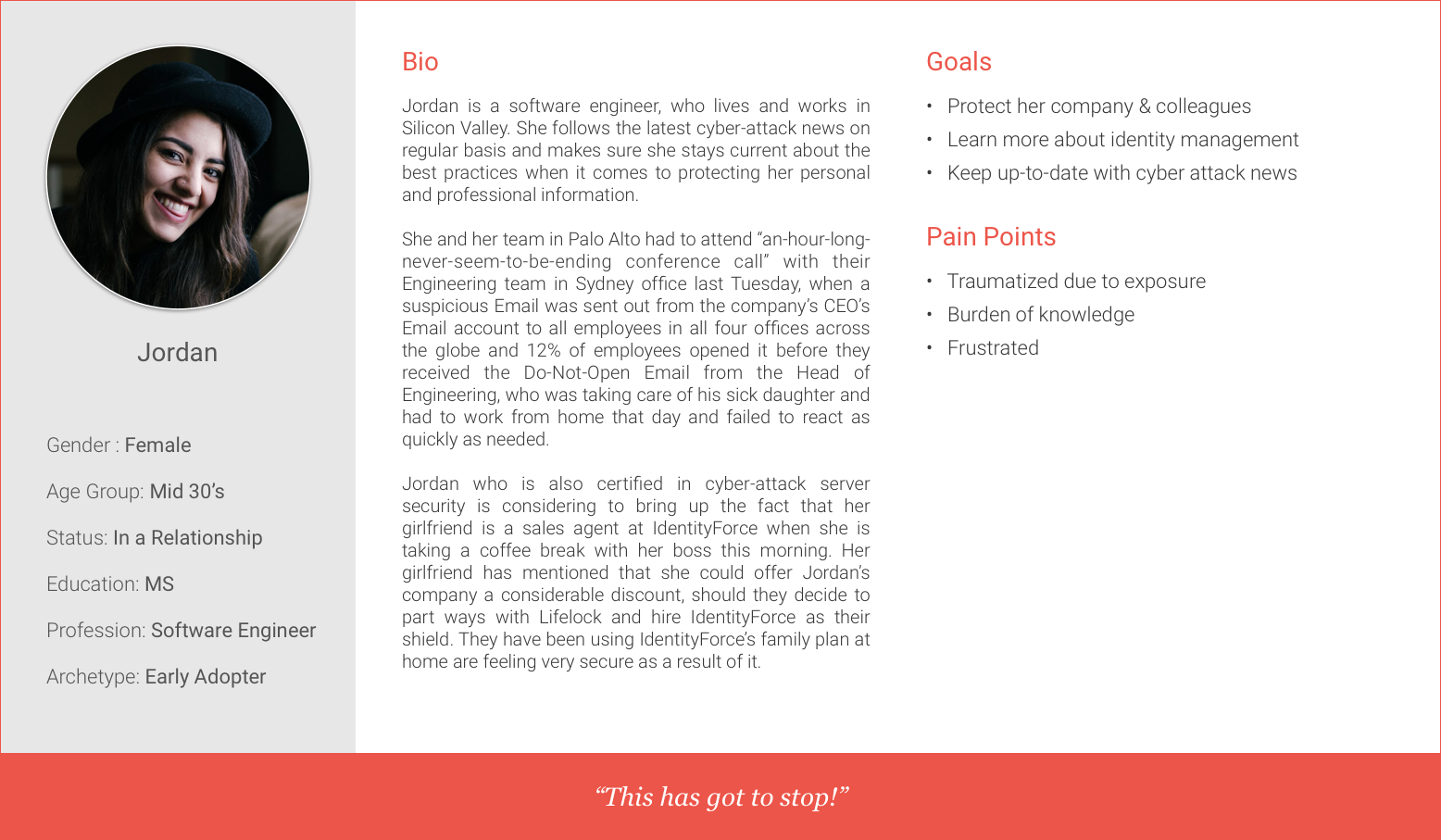
We created four categories of people (personas) that could be using our App:
Primary Personas:

Secondary Personas:

IdentityForce’s New & Improved Native App
In the interest of our short time, and since IdentityForce’s main concern was to find new ways to engage unmotivated users, we focused on our primary personas. We also knew that if we meet our primary persona’s needs we have met our secondary persona’s needs as well.
Features
If you would ask three Designers to come up with a long list of features, there would NOT be any shortage of ideas. We started with a laundry list of features that could or could not be realistic and achievable, and had a lot of fun along the way...
Minimum Viable Product (AKA MVP)
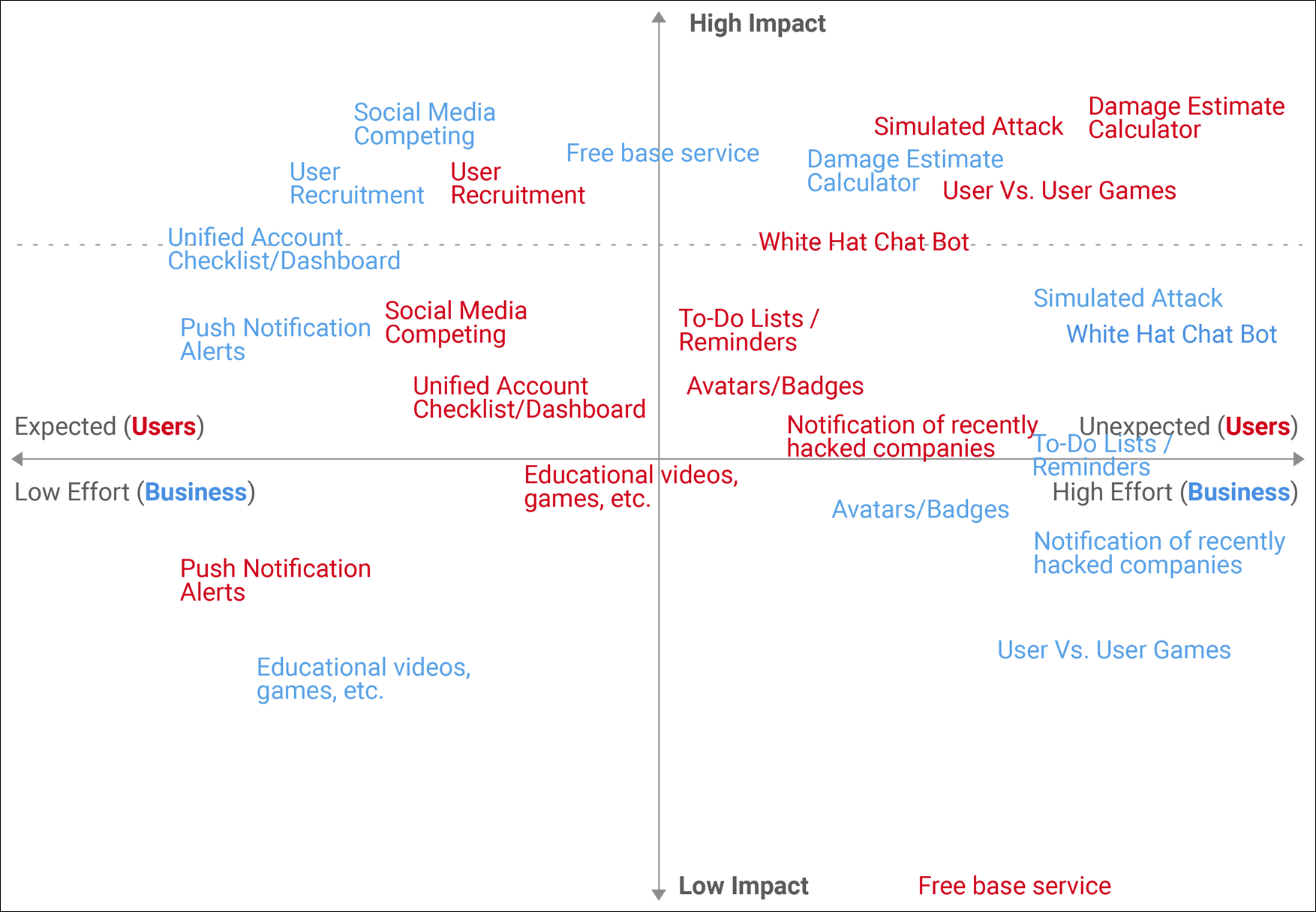
Then it was time to get a reality check and decide on a minimum viable product (MVP) that would meet both users and business needs. Following are the features we agreed on:
1) Educational (Videos, Games, etc.)
2) Unified Account Checklist/Dashboard
3) Avatars/Badges
4) Quest List / Reminders (Things to Do) / To-Do Lists Alerts / Gamifying Password Changes / Checklist
5) User Vs. User Games
6) Simulated Attack (email verification, activity verification, or location, situation, etc.)/Investigation Service Simulation
7) User Recruitment or Drafting
8) White Hat Chat Bot
9) Social Media Competing (with or without badges)
10) Push Notification Alerts
11) Damage Estimate Calculator
12) Free Service & Premium Service
13) Notification of Hacked Companies
IdentityForce Mobile App
Feature Prioritization Matrix
User Flows
We created two scenarios, in which our main two personas would start using and exploring IdentityForce’s New App:
Scenario 1
Kwame tells his friend, Patrick, that he is not taking any actions in protecting his identity, even though he has been a victim of identity theft before. Patrick has an IdentityForce account and encourages him to be more proactive, as he does not want Kwame to have to go through the trouble of having to recover from identity theft again. He sends Kwame an email invite to download and start using IdentityForce’s Mobile App.
Scenario 2
Cara was dealing with a particularly heart-breaking case of identity theft at work. Her client’s child had his credit destroyed by a hacker. Cara confided to her colleague, Lynda, that she was terrified of this happening to her family. Lynda recommended that Cara would start using IdentityForce to learn about how to protect both herself and her loved ones.
IdentityForce Mobile App
Onboarding & App User Flow
Paper prototyping
Based on our MVP features above, we did two rounds of design studio, where we all started sketching our ideas and how we thought we would visualize the 7 features, and then shared with the team. After that, it was time to combine our ideas and conducting a few sessions of usability testing.
IdentityForce Mobile App
Paper Prototypes
Usability Testing
During our usability testing, we realized that users liked our story, but not the flow. We were asking users to register on our App and complete a short self-assessment without even showing or telling them what our App had to offer. We resolved this issue by changing the order of our flow as well as improving our content by telling our users, should decide to register, what we were going to do with the information they would provide and how we would help them protect their identity.
IdentityForce Mobile App
Usability Testing
Wireframes
Once we gathered our insights from usability testing, it was time to move to digital wireframing on Sketch. We divided task and we each created wireframes that would tell a different part of our story. I focused on the App screens after users have registered and before they would enter the game portion of the App.
User Interface
We chose Material Design as the style for our User Interface. We all were lifelong iPhone users, and to challenge ourselves, we chose to design for Android first.
InVision Prototypes
We transferred our screens to InVision App and created two prototypes for the native mobile App and the game environment, where users would learn best practices in identity protection, in a horizontal tower defense style game.
Presentation
We presented our process and solution to a class of 30 students and three instructors and got very positive feedback.
More Usability Testing
We showed our prototype to a few students on campus, in addition to one of the users who had given us feedback on our early stage paper wireframes. This time, people had a better understanding of what we were trying to achieve and told us they would consider using our App if it were built.